YOUR SECURITY
Security for your home network is crucially important. The internet as it exists now is a lot like the wild West. As we speak, scanners are sweeping through the list of addresses that contain your router, and when they find it, they unleash a series of probes than can only be described as a spirited door-jiggling session.
Others want access to your network for so many reasons: identity theft, stealing banking and financial information, PC's for their botnet, PC's to encrypt for Ransomware attacks, and so many more horrible things. It's up to you to make your network as safe as possible. I liken network security to car theft. Any car can be broken into and any network can be breached. But if you make them difficult to do, bad actors will move on to easier pickings. Here's how to increase your network security and make it as difficult as  possible to successfully attach your network.
possible to successfully attach your network.
YOUR ROUTER & SECURITY
To begin increasing security, you need to go into your router's administration and make a few changes. To get into your routers administrative area, in a web browser for the URL type 192.168.1.1 (or if that doesn't work 192.168.0.1). That should bring you to a page asking for credentials. These are the same credentials you set up when first configuring it (you wrote them down or used a password manager, didn't you?). Once inside the first thing is to change the default admin credentials, and use a strong password! Your router password should be between 16 and 20 characters long and complicated. FYI you absolutely should be using password manager software to manage all of your passwords.
While inside your router's administration area, disable WPS (WIFI protected setup) as well as UPNP. WPS is an easy way to add devices to your network and can be abused. UPNP (Universal Plug and Play) is also a way to simplify adding devices to your network and it can be hacked. Disable both please.
You also want to disable remotely accessing your router's admin controls. If you do so then only someone on your network can access the router's admin functions.
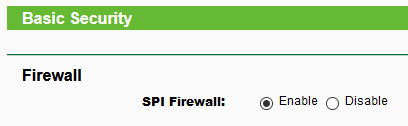 Check the area of your router regarding its built-in firewall and be sure that it's enabled. If your router does not have a built-in firewall, you can purchase one separately (or buy a new router!). Here's a review of home firewalls. I have to say however that I'm a fan of integrating the firewall within the router. A separate firewall adds a layer of increased complexity that might confuse the average home user. And as PC Magazine states, "In the modern world, there's hardly ever a reason to consider installing a standalone personal firewall."
Check the area of your router regarding its built-in firewall and be sure that it's enabled. If your router does not have a built-in firewall, you can purchase one separately (or buy a new router!). Here's a review of home firewalls. I have to say however that I'm a fan of integrating the firewall within the router. A separate firewall adds a layer of increased complexity that might confuse the average home user. And as PC Magazine states, "In the modern world, there's hardly ever a reason to consider installing a standalone personal firewall."
Also, keep your router's firmware up to date. Check to be sure there's not an updated version out there. Updates patch security vulnerabilities. Keep it patched!
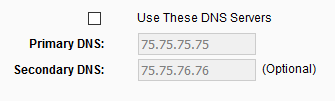 Change your DNS. A DNS, or Domain Name Server, changes internet names like www.google.com into their computer's IP address, so it's absolutely necessary for web surfing. Every time you type a URL into your browser your computer looks to a DNS server to see what address that name is. By default, your internet connection probably uses a DNS server from your ISP. This is not optimum and gives your ISP a ton of info about your web surfing habits (which they unscrupulously retain and sell). There are DNS servers out there that are much better for security and privacy and faster as well, so switch to one of those.
Change your DNS. A DNS, or Domain Name Server, changes internet names like www.google.com into their computer's IP address, so it's absolutely necessary for web surfing. Every time you type a URL into your browser your computer looks to a DNS server to see what address that name is. By default, your internet connection probably uses a DNS server from your ISP. This is not optimum and gives your ISP a ton of info about your web surfing habits (which they unscrupulously retain and sell). There are DNS servers out there that are much better for security and privacy and faster as well, so switch to one of those.
WIFI
In the wireless section, to ramp-up security the first thing you want to do is to change your WIFI SSID (the name that your router broadcasts your signal). You don't want to leave it default, as hackers can learn what type of router you have from that. Nor do you want to rename it something identifiable to you, ie "TOM'S WIFI". Any scrap of real data you give to hackers is one step closer to identity theft and/or hacking your network.
Use wireless encryption, WPA2 with AES is the best. TKIP is better than nothing at all, but if you can, use AES (until WPA3 becomes available in devices, very soon).
You might want to turn on guest access which allows visitors to access your WIFI without accessing your password and it also limits your network info that leaks out. It can limit damage when an infected device plugs into your network also and you can use guess access to connect your IOT devices (Internet of things) which protects your core network.
And by the way, if you're going to be gone from your home for a length of time, turn off your WIFI. How secure is it to leave it on when no one is using it giving hackers more time to crack in?
VPN
For security, you need a VPN. "What's a VPN?" you might ask. It's a virtual private network, and here's how it works. You load software onto your computer from a VPN provider that you pay for their service. When you start the VPN software, it creates a virtual private encrypted "tunnel" of all your internet traffic between your computer and one of the servers that the VPN company operate somewhere in the world. You can usually select which city you want to connect your traffic to before you start the VPN. When you start it, all of your traffic is encrypted and sent to the VPN server in that city where it's decrypted and sent out onto the public internet. Because it looks like your traffic is coming from the VPN server in that city, your own IP address is hidden. This is a really good thing as then no one will be able to know where you're located. With a VPN, your ISP cannot know what exactly you're doing and log your actions. It's completely in the dark about you internet activities which is how it should be (without a VPN, then know everything you do and often sell that data to advertising companies and others). However, now the VPN company has as much info about your internet activities as your ISP used to. When investigating which VPN to buy, make sure they never sell your data and retain as little info about you and your activities as possible. Check their privacy policy. The best VPN's have a "NO LOG" policy, that is, they don't retain any identifying information about their users or their users activities.

Then there's the question of what country the VPN company is located in. This is important for privacy purposes because of the 5-eye alliance. In a nutshell, in the 1950's, the US and England entered into an intelligence-sharing alliance. In the late 50's Canada, Australia and New Zealand joined this alliance: the "5-eye" alliance. This agreement has extended to the surveillance of online activity. Edward Snowden's revelations exposed the fact that there is widespread government surveillance of online activity, and much data sharing between the 5-eye countries. Since then there have been two additional international intelligence-sharing agreements (known as "9-eye" and "14-eye" agreements). The people at VPN Mentor have created this chart showing all these countries (left).
What exactly does this have to do with you? If you're concerned about online privacy, you don't want to use a VPN based in any of the 14-eye countries. If you do, your VPN provider could be forced to hand over data about it's users, and that data shared between the 14 countries. The world is a big place, choose a VPN located somewhere else.
The average cost of a well-rated VPN is about $10/month, though they can be had for much less or much more. As the saying goes, you get what you pay for. If it costs more it should be offering more in return, like more locations around the world. Don't lock in to a long-term contract unless you tried the companies services at length and are very happy with the service. Make sure it can connect multiple computers at a time (minimally five) and also make sure that it can handle bit torrent traffic (most do).
When and what to use a VPN for? Some people use it to bypass geoblocking. For instance Netflix puts geographic restrictions on the content that you can see based on where you are. Netflix content in Europe will be different than Netflix content in America. Because a VPN connection can appear to come from anyplace that you want (within the constraints of your VPN company), it's possible to VPN to a European location and access Netflix's European content. It's more complex than that of course, but many people use VPN's to bypass geoblocking. Here's the URL of Netflix when logged in normally, and when logged in using a VPN Tokyo connection:
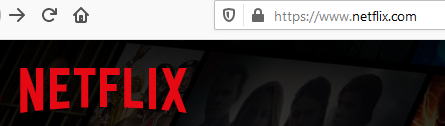
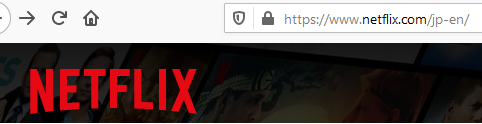
Some people use VPN's to save money by doing online purchasing in different areas around the world where pricing is different than where you are. This is especially true of traveling, where flights and hotels can be had for much different rates than what you see from your location.
Some people use a VPN to increase their connection speed, though I have not experience this. In fact I find the VPN sometimes slows my connection. It is said however that a VPN will improve speed if your network is congested or your ISP practices throttling.
My normal network speed is 120 mbps. here it is when connected to Los Angeles and Tokyo:
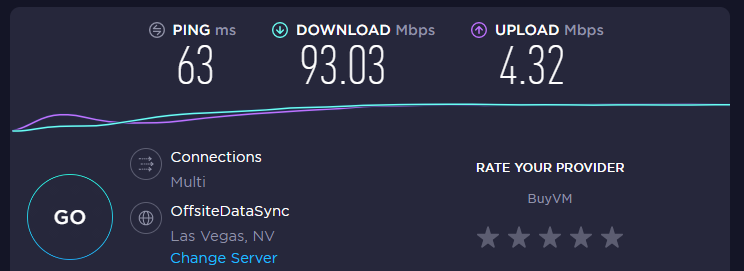
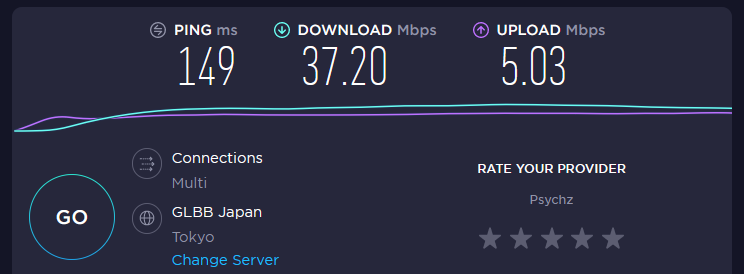
Some people feel that financial transactions are more secure using a VPN, though there are some issues with this. "If PayPal detects that you are using a VPN, it will lock your account to prevent it from being hacked by cyber-criminals." Some banks will do this too. One of the ways around this is to connect to a VPN server in a nearby city so it doesn't look as if your connection is coming from another country.
And some people use it to prevent their ISP from snooping on their web activities.
Bottom line - it's not a bad practice to run your VPN all the time, especially if you're concerned about privacy and security. And if you are traveling with your laptop you should always be using a VPN to connect.
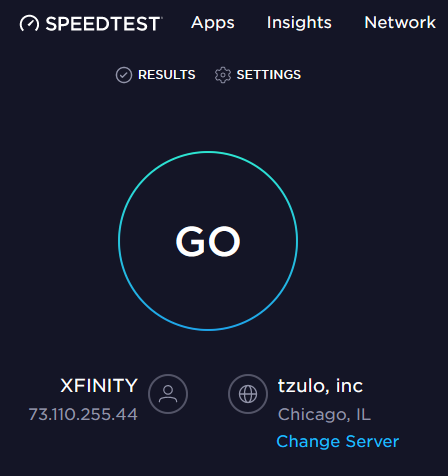
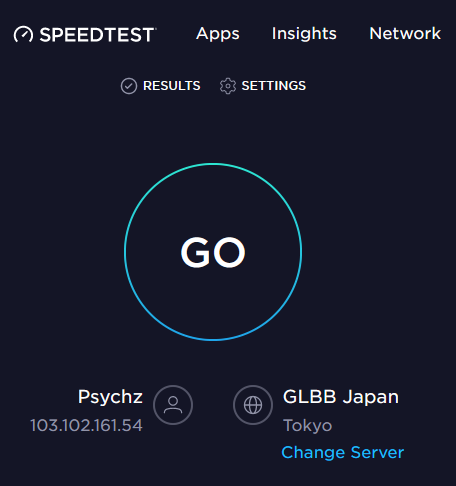
PRO VPN tip: I have had the experience of leaving a VPN running for a long time, only to have the software fail in the background, essentially dropping my privacy shield without me knowing it. To see what's happening, I periodically go to speedtest.net because it shows the closest server that they use to connect to. Here you can see what it shows when I'm not using a VPN and when I'm VPN-connected:
IPv6
Initially I was going to tell you to turn off IPv6 in your router(if it can do so). I have had problems in the past with Comcast and IPv6 and have turned it off. But now I've turned it on because the benefits outweigh the problems, and the benefits only increase over time.
In a nutshell, available unique IP addresses ran out along ago. The internet IP address format that we're familiar with: 123.456.789.987 - has a finite amount of unique numbers. They are 32-bit numbers displayed in a dotted decimal format and this whole addressing schema is called IP4. The maximum number of unique addresses is about 4.29 billion and all of them have been allocated. Then why hasn't the internet come to a halt? Because there's a number of workarounds. For instance, each device on your network does not have a unique internet address. Remember that behind a router, all networks have addresses in the format 192.168.x.x. So basically your network only needs one unique internet address - one for your router - and it handles the rest. But this isn't the greatest thing int he world because devices behind the router aren't directly accessible (symmetric) so more workarounds come into play.
IPv6 was created to alleviate these issues and provide a lot more numbers. IPv6 uses 128-bit numbers, and there are 340,282,366,920,938,000,000,000,000,000,000,000,000 or 3.4 x 1038 unique ones, so it should be a long time before running out. The switch from IP4 to IPv6 has been going on for a decade or so, but slowly. Most things are still using IP4 addresses and the two systems communicate via special gateways. It's a huge job but its gaining steam as we speak.
I was going to tell you to disable IPv6 because of possible IPv6 leaks; that is, allowing someone to determine your actual IP address by the address "leaking" in VPNs via IPv6. Turns out, that should no longer be a problem. What you really want to watch for when using a VPN is WebRTC leaks.
WebRTC stands for 'Web Real-Time Communication" and allows for voice, video chat and p2p sharing within the browser without an extension. A WebRTC leak is when your IP address is exposed via your browser's WebRTC, even when you're using a VPN. Not good!What to do?
Go over to restoreprivacy.com and lear now to plug WebRTC leaks...it's not difficult. As the article says, when your all set and have your VPN running, go over to ipleak.net to test whether you have any leakage going on. Here's what it said about my computer after I established a VPN to Dallas:
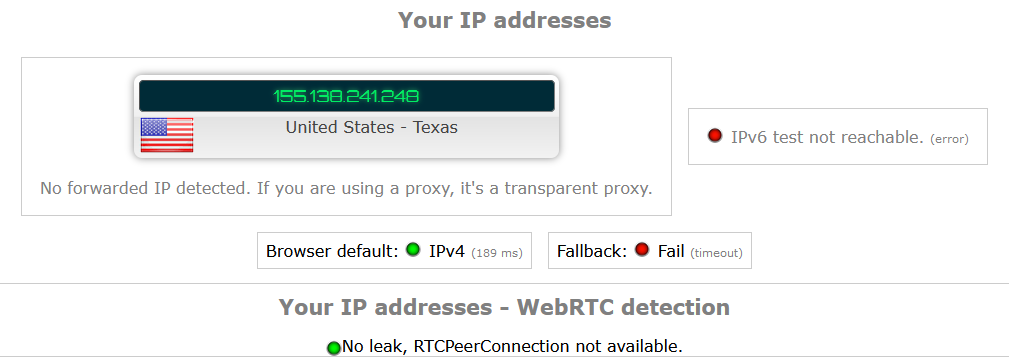
Not so bad! But I still have some DNS leaking I have to track down...
COMPREHENSIVE SECURITY SOLUTIONS
Do you need one? By this I mean one of the products that are sold my anti-virus makers that normally include a ton of other things, from firewalls, ransomware protection, sandboxing, secure browsers for financial transactions, spyware and more. This is a nuanced question. Microsoft Windows itself usually does a good job of protecting and securing Windows. If that's your goal I'd say that you probably don't need these products (or a simple anti-virus without anything else). But some consider these security suites as multilayered protection in-depth, highlighting and protecting against various specific threats. This is probably true and I'd say that a computer with a well-rated security suite installed is probably safer than one without. But does the safety justify the cost? FYI I say cost because under no circumstances would I install a free anti-virus product. Turns out there are ones that are free because they do things like sell our web-browsing history to whoever wants it (Hello Avast!). In fact they have a whole list of dubious behaviors and you should avoid them like the plague. One anti-virus company even acted to help a government steal classified US data!
Bottom-line, if you feel that you need extra security, by all means purchase and install one of the better-rated security suites out there. But without one, Windows is doing fine in protecting itself.
GEOTAGGING
When you take a picture with your phone camera (and probably standalone cameras) the device notes your GPS coordinates and embeds them into the photo's metadata (called EXIF), ie geotagging. This can be a privacy concern in that complete strangers can learn your location through these photos. Amazingly, most social media strip out all the metadata when you're uploading. This includes Facebook, Instagram, and Twitter as well as Reddit and Imgur. Pretty much the only sites that don't automatically strip out this info are photography sites like Flickr. They will give you the option to remove this info though and if I were you I'd take it. the less information about you out in the wild the better.
Note that Twitter strips out your pictures geolocation info, but may well geolocate your tweets. here's how to stop that from happening.
